
Around the globe, cybersecurity is prompting serious dialogue. The challenges are immediate and well-known, but the ingredients for more effective cybersecurity are within our grasp. As with so many things, cybersecurity is a collective goal that will only be met with collective action. It's bigger than any one company, any one legislative body or any one international body.
This conclusion is informed by years of trials and tribulations that the computing industry has faced together, and an appreciation for the innovations that others have made. It's a conclusion that those in boardrooms, legislative halls and international institutions around the globe are arriving at as well.
In this light, it's important to understand two of the elements that are shaping our collective response to cybersecurity challenges: an increasingly data-centric society and the role of government.
Data-Centric Society
In a world of increasingly integrated devices -- whether it's your car syncing with your phone or an app saving your jogging stats to the cloud -- data is constantly being generated. This data-richness of society's communications has fundamentally rewritten the structure of the Internet. To illustrate, compare these two depictions: the first representing the World Wide Web in 1990 and the second representing the Internet of today:
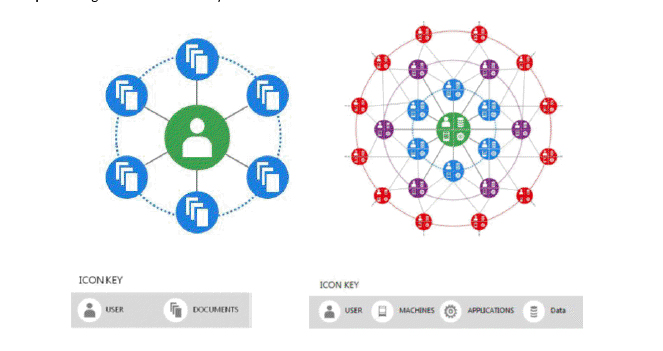
To say the increasing intricacy of our communications has complicated cybersecurity is an understatement.
No longer is the architecture of the Internet largely limited to users accessing specific documents. Today, we have far richer interactions, with numerous other machines, networks, applications and data. The result is a far greater surface area for malicious activity -- it's a world where the threats are no longer linear.
This reality creates especially poignant challenges for governments trying to craft cybersecurity policies. Dependence on IT systems continues to grow, and both the number and sophistication of cyberattacks are also increasing. Although there is broad recognition that security of these IT systems must improve, there are disparate views, both within countries and among them, on the role of government in driving those improvements.
The Role of Government
With the recent spate of high-profile cybersecurity policy activity in the United States and Europe, it's clear that governments are taking cybersecurity seriously. No doubt, governments have a responsibility to protect the Internet and its users; they cannot sit on the sidelines. They also cannot ignore political and cultural differences and seek a single one-size-fits-all solution. But even if cybersecurity policies vary on a nation-by-nation basis, they should adhere to a common set of principles that foster Internet growth and innovation, enable the best cybersecurity outcomes, and respect national and international interests. More specifically, governments should do the following:
Integrate the private sector into national and international efforts to enhance cybersecurity. The bifurcation of responsibility (governments must protect national security and public safety) and control (governments do not design, deploy or operate the assets that must be protected) dictates the need for public-private partnership at both the national and international level with clearly defined roles and responsibilities.
Promote cybersecurity policies that are technology-neutral and innovation friendly. Such policies should not endorse, require or otherwise advance a particular technology product to the exclusion of others; rather, they should identify desired outcomes and allow the marketplace to find the most innovative way to achieve those outcomes.
Anchor their approach to securing IT systems in risk management. This includes narrowly scoping what systems are truly critical for national security and public safety, and defining security outcomes that enable organizations to be flexible in addressing risk in a dynamic cyberthreat environment. By leveraging risk management principles, limited resources can be directed to where they will have the greatest impact.
Encourage dynamic information sharing, focused on addressing specific challenges. Information sharing efforts should focus on solutions that facilitate sharing within industry, among government and industry, and from government to government. Targeted information sharing (that is, sharing the right information with those who can meaningfully act on it) better protects sensitive information (whether in the hands of the government or private sector), helps preserve privacy, and actually permits more meaningful sharing of data.
Continually keep in mind the global and international ramifications of their actions. It should be recognized that limiting markets based on cybersecurity concerns can lead to reciprocal behaviors and potential fracturing of the Internet. This in turn would limit the benefits that come from globally connected devices and services. International engagement will foster shared understanding and common views that can bring greater order and predictability to a very dynamic landscape with many different actors, state and nonstate.
If governments adopt such principles, they will promote a cybersecurity posture that fosters continued innovation and builds a framework for ongoing dialogue. Today's security outcomes and tomorrow's computing experiences will benefit as a result.