Lead, follow or get the heck out of the way
In peacetime the U.S. military is an immovable and inflexible bureaucracy. In wartime it can adapt and adopt organizational change with startling speed.
BMNT, a new Silicon Valley company, is combining the Lean Methods it learned in combat with the technology expertise and speed of startups.
---
But first some history...
World War II
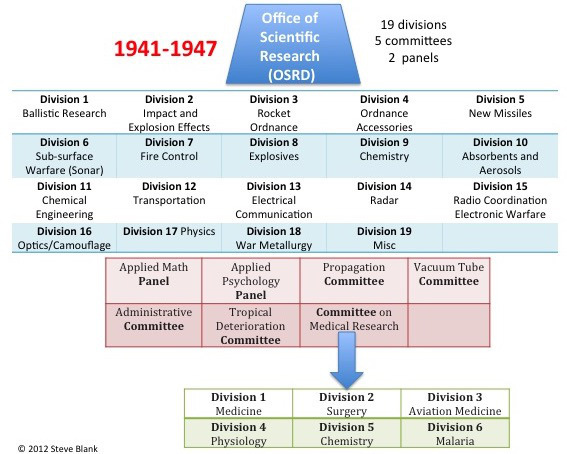
In World War II the U.S. government reengineered its approach to building weapons. In a major break from the past, where the military designed all its own weapons, 10,000 scientists and engineers from academia worked in civilian-run weapons labs (most headquartered in universities) in an organization called the Office of Scientific Research and Development (OSRD).
OSRD was tasked to develop military weapons systems and solve military problems but had wide autonomy to determine how to accomplish its tasks and organize its labs. (The weapons were then manufactured in volume by U.S. corporations.)
The OSRD developed advanced electronics: radar, electronic warfare, rockets, sonar, proximity fuse, Napalm, the Bazooka and new drugs such as penicillin and cures for malaria. One OSRD project - the Manhattan Project - the development of the atomic bomb - was so secret and important that it was spun off as a separate program. The University of California managed research and development of the bomb design at Los Alamos while the US Army managed the Los Alamos facilities and the overall administration of the project.
After the war the U.S. split up the functions of the OSRD. Nuclear weapons went to the new Atomic Energy Commission (AEC), basic weapons systems research went to the Department of Defense (DOD) and all U.S. biomedical and health research went back to the National Institutes of Health (NIH). In 1950, government support of basic science research in U.S. universities became the charter of the National Science Foundation (NSF). Each of these independent research organizations would support a mix of basic and applied research.
The Cold War
During the Cold War the U.S. and the Soviet Union faced off with a nuclear deterrence policy called mutually assured destruction (aptly named MAD.) But to fight a conventional war in Europe, Soviet forces had built a 3 to 1 advantage in tanks, artillery, armored personnel carriers, and soldiers. In response the U.S. developed a new strategy in the late 1970's to counter the Warsaw Pact. Instead of matching the U.S.S.R. tank for tank or solider to solider, the U.S. saw that it could change the game and take advantage of a lead we had that was getting longer every day - using our computer and chip technology to aggressively build a new generation of weapons that the Soviet Union could not.
At the heart of this "offset strategy" was "precision strike," - building stealth aircraft to deliver precision guided munitions unseen by enemy radar, and designing intelligence and reconnaissance systems that would target for them. The offset strategy was smart weapons, smart sensors, and stealth using silicon chips, electronics and computers that only the U.S. could design and produce.
By the mid-1980's the Soviet military was struggling to keep up with this "revolution in military affairs." The announcement of the Strategic Defense Initiative (Star Wars) further destabilized the Soviet Union.
The Gulf Wars
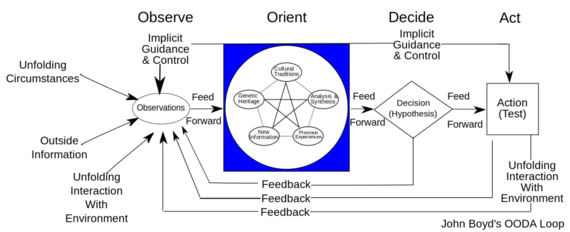
When I first started teaching customer development (searching, validating and executing a business model), one of my students pointed out that customer development was similar to the theory of a military strategist, John Boyd. In the 1960's, Boyd, who was a fighter pilot, proposed that instead of executing a fixed plan, wars would be won by those who can Observe, Orient, Decide and Act (the OODA Loop.) After being ignored for decades, Boyd's OODA Loop drove the U.S. war fighting strategy in both Gulf Wars. The OODA Loop was the Lean Startup philosophy before lean.
Iraq, Afghanistan and the Army's Rapid Equipping Force (REF)
In Afghanistan in 2002 U.S. soldiers were tasked to clear caves that the Taliban used to store equipment. Many of the caves still had Taliban fighters inside while others had been booby-trapped. To clear the caves soldiers threw grappling hooks inside then pulled the hooks out to catch trip-wires and explode bombs. But often this technique did not work and soldiers died. The Army realized they needed to do something more effective. They gave the problem to Colonel Bruce Jette, and 90 days and $750,000 later he had bypassed the existing Army acquisition system and bought existing robots from companies. Exponent provided the PackBot and the Marcbot and deployed them to the field.
From that day the Army's Rapid Equipping Force (REF) was born.
The REF's goal is to deliver technology solutions to front-line soldiers in days and weeks, instead of months and years either by using solutions from previous REF efforts or existing government- or commercial-off-the-shelf technologies purchased with a government credit card.
The REF had permission to shortcut the detailed 100+ page requirements documents used by the defense acquisition process. It developed a ten-line short form that listed the most important parts of the requirement. The REF also had its own budget, which it could use to acquire equipment.
Soon the REF was sending teams of civilian and military subject matter experts out into the field to discover what they needed. REF expanded its operations to include forward teams in Kuwait and Iraq to provide technology to fill capability gaps and to counter the highest priority threats.
By the end of 2007, the REF had delivered more than 550 types of equipment and more than 75,000 individual items. The average time from receiving a request from the field to delivering a solution to the soldiers was 111 days.
In 2010 Colonel Peter Newell took over the REF and turned its focus into what we would call a Lean Startup.
Newell insisted that REF started with a deep understanding of soldiers' problems before purchasing a proposed solution. Newell found that four problems accounted for two-thirds of REF requirements:
- defeating roadside bombs
- supporting soldiers on foot with communications and load carrying devices
- providing soldiers with timely intelligence, surveillance, and reconnaissance in combat
- supplying and protecting small isolated combat outposts
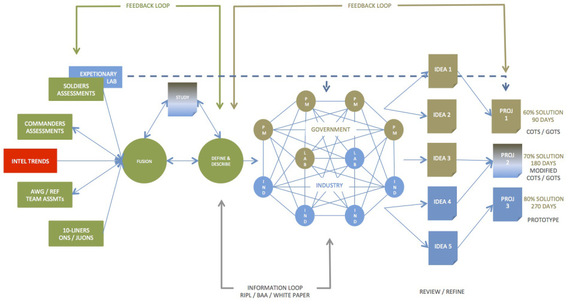
He came up with his version of the OODA loop to explain to people how REF should behave.
To get closer to his customers, Newell commissioned three mobile laboratories that were airlifted to forward operating bases. These labs included a Computer Numerical Control milling machine and 3-D printers for rapid prototyping.
Hacking For Defense (H4D)
When Colonel Peter Newell left the Army, he came to Silicon Valley at the urging of a friend and fellow retired Army Colonel, Joe Felter, a Stanford PhD who moved to Palo Alto and Stanford after a career in the Special Forces. Newell accepted Felter's invitation to join a company he had originally established. BMNT does for the Department of Energy, the Department of Defense and the Intelligence Community what the REF did for the U.S. Army - build teams that deliver solutions to complex problems, with access to the entire network of suppliers and partners that Newell and Felter developed throughout their careers.
To tap into the innovation of Silicon Valley, BMNT, in collaboration with Stanford's Preventive Defense Project organized Hacking For Defense (H4D) - a series of hackathons - to help the Department of Defense do four things:
- Identify new ideas that will solve problems the military expects to see in the future
- Map those ideas to the technology that could be used to solve them
- Recruit the people who can make it happen
- Show the DoD how to engage Silicon Valley with challenging problems and build networks of people to solve them
BMNT's first hackathon, "Hacking the Supply Chain," brought together diverse teams of technologists and users to provide solutions to the questions: How do you supply troops which can be sent on short-notice, for long periods to places where there are no existing bases or supplies? How might we create the most resilient and efficient supply chain possible for our forward-deployed land forces in 2025?
- energy and power generation
- potable water and field expedient sewage systems
- advanced manufacturing and repair maintenance technologies
- training and readiness technologies
- command, control, computers, and communications technologies
In mid-April, the ideas generated at BMNT's first hackathon will be presented to a panel of experienced senior entrepreneurs, engineers, and military and government officials and then sent to the Department of Defense with specific recommendations on the technologies with potential to support them.
Ultimately Newell and Felter say they want to use BMNT to create an "insurgency" in Silicon Valley to get cutting-edge innovation into the organizations defending our country. (Click here for information on Hacking for Defense events.)
Hacking the Prime's
In reality, what BMNT is trying to fix is the way the Department of Defense acquires radically new technology and ideas. While DARPA tries to fill that need, today the primary conduits for bringing new technology to the government are the prime contractors (e.g., Lockheed, Boeing, Raytheon, Northrup Grumman, L3, General Dynamics, et al.) But most of these contractors focus on fulfilling existing technology needs that can be profitable.
If a startup wants to provide new technology to the Department of Defense (DoD), they have to sell through the prime contractors who own the relationships with the DoD. Most startups and innovative companies are unwilling to risk exposing their Intellectual Property and go through the paperwork of dealing with the government, so they choose not to pursue government ventures. In this way, the primes artificially restrict DoD's technological funnel. (Palantir is the most visible Silicon Valley insurgent in this space.)
Today, incentives for bringing innovation into the government with speed and urgency are not aligned with the government acquisition, budgeting, and requirements process. As a result, the DoD fails to acquire truly innovative technologies (much less paradigm-changing technologies) in a timely fashion.
- In peacetime the U.S. military is an immovable and inflexible bureaucracy
- In wartime it can adapt and adopt organizational change with startling speed
- The Rapid Equipping Force operated with speed and urgency to deliver solutions to real customer problems
- BMNT and Hacking for Defense are trying to bring this same process to Silicon Valley
Steve Blank's blog: www.steveblank.com