"Stellar Wind," a National Security Agency (NSA) secret program, collected more than two years of email and Internet data, the Guardian is reporting in its latest revelation about Obama Administration "secret surveillance."
A year before Edward Snowden disclosed the NSA metadata collection program, we knew employers have new ways to monitor email data.
Social network expert Marc A. Smith told a meeting of journalism and mass communication professors in Chicago that the same technologies used to visualize social networks may be used with email data. While Germany limits what employers may access, he said, the U.S. has no such privacy data protection laws.
In the public domain, Smith said computers could read 130 million tweets per day. At the time of Smith's talk, we had no way of knowing the Obama Administration's government interest in sweeping our phone, email and Internet records.
Here is how social network analyses can provide information on associations with others, engagement within a network and flow of communication. As an example, our Omaha research team last month used the NodeXL software, which sits as a template on top of Microsoft Excel spreadsheets, to study the #BRK2013 hashtag on Twitter during the 2013 Berkshire Hathaway annual meeting hosted by CEO Warren Buffett, his board and their companies. Universal Information Services, our research partner, is whitelisted on Twitter with the ability to scrape thousands of data points.
The visualization that emerges is instructive.
From studying the social network map, we learned that four of the top 10 influencers during the annual meeting had associations with the CNBC cable channel, but business news anchor and reporter Becky Quick, a Buffett favorite, was not the top tweeter. She was eighth most influential behind Andrew Sorkin, a columnist for the New York Times and CNBC Squawk Box, who was first. The Motley Fool and the Times' Dealbook sites also were among the top five.
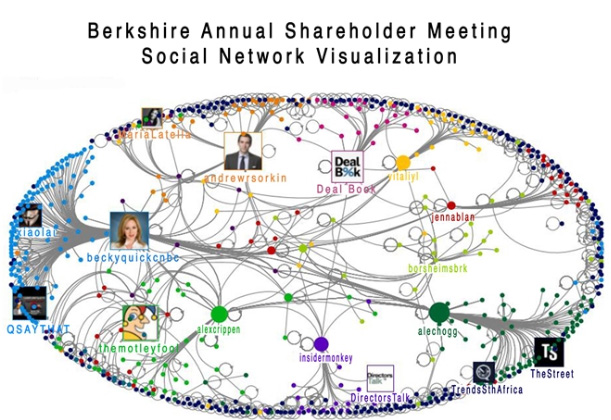
The social network map shows about four significant sub-networks all feeding a large audience during the international media event.
Now, imagine a boss at your company creating a similar visualization out of your Microsoft Outlook email system. Smith says an employer might use such data to determine who is at the center of a social network and who is at the periphery. During a round of layoffs, the data might show who the company could live without.
So, it is not much of a leap to see why the NSA would be interested in big data. If your job were to search for terrorists, then you would like to examine the character of their social networks. If you could identify leaders, then you might be able to stop a plot before it happens. As communication moves online, it is easier to observe.
This is why technologists declare that privacy is dead. To the extent that we use technology in our daily lives, we should expect that monitoring is inevitable. It's also why we should urge lawmakers to approve clear boundaries and limitations on telephone and email data collection and analyses by employers and the government.
